8.8 KiB
8.8 KiB
- Introduction
- Security Requirements
- Security Policies and Models
- Practical Security Engineering
- Security Mechanisms
- Security Architectures
Introduction
Risk Scenarios
Reducing Operational Risks: What responsibilities can we bear?
Critical Properties
- Security + Safety
- Reliability
- Correctness
- Availability
- Real Time
- Scalability
- Openness
Examples:
- Information Systems
- Communication Systems
- Energy Grid Management
- Traffic Management
- Consumer Technology
Responsibility for risks -> guaranteed properties!
Relevance of Security: Security properties if any IT system are mission-critial - independet of its application domain
Security Goals
Our Faculty's Education and Examination Management System
- Maintains:
- Course profiles (examination form/date, credit points)
- Students records (personal data, registration to examinations, grades)
- Services:
- Enrolment/expulsion of students
- Registration to examination
- Registration of examination marks
- Information and attestations desk
- Operational Risks
- Conditio sine qua non: Provability of information properties
- Fake registration to examinations: integrity, non-repudiability ("nicht-abstreitbar")
- Leakage of grades, personal data: confidentiality, integrity
- Forgery of attestations: authenticity, integrity
Industry Control Systems
- e.g. Factorys, energy and water plants (public infrastructure)
- "Chinese Hacking Team Caught Takin over decoy water plant"
- "Internet Attack shuts off the Heat in Finland"
- Operational risks: Integrity & Availability of public community support systems
Self Study Task Read about these two scenarios. Find one or more recent examples for attacks on public infrastructure, including some technical details, in the news. Keep all these scenarios in mind, we will come back to them in the next chapter:
- Hacker breached 63 universities and government agencies
- Ransomeware attacks on public services
- Unsecured Databases
- Worst data leaks and breaches in the last decade
Message
- Goal of IT Security: Reduction of Operational Risks of IT Systems
- Elementary: Protection of
- Confidentiality
- Integrity
- Availability
- Non-repudiability
Specific Security Goals: Terms
- Confidentiality: the property of information to be available only to anauthorized user group
- Integrity: the property of information to be protected against unauthorized modification
- Availability: the property of information to be available in an reasonable time frame
- Authenticity: the property to be able to identify the author of an information
- Non-repudiability: the combination of integrity and authenticity
| Safety | Security | |
|---|---|---|
| Goal | To protect environment against hazards caused by system failures | To protect IT systems against hazards caused by malicious attacks |
| Technical failures: power failure, ageing, dirt | Industrial espionage, fraud, blackmailing | |
| Human errors: stupidity, lacking education, carelessness | Terrorism, vandalism | |
| Force majeure: fire, lightning, earth quakes | ||
| => making sure things work | in the presence of system failures | in the face of an intelligent and maliciousadversary |
Security Engineering
Security Goals in Practice
- ... are diverse and complex to achieve
- ... require multiple stakeholders to cooperate
- ... involve cross-domain expertise
Security Engineering:
- Is a methodology that tries to tackle this complexity.
- Goal: Engineering IT systems that are secure by design.
- Approach: Stepwise increase of guarantees -> formal methods required!
Steps in Security Engineering:
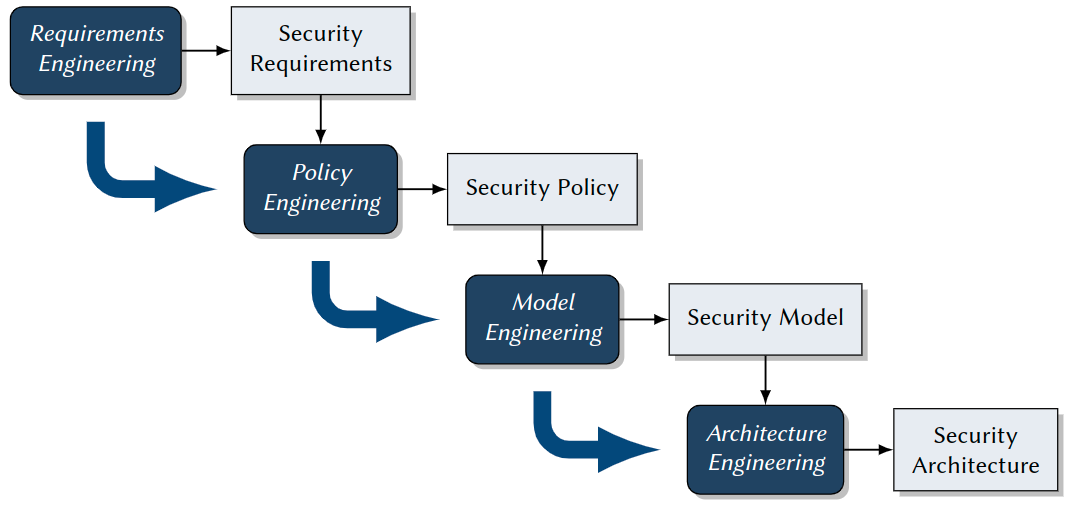
Lecture Roadmap
- Security Requirements: Vulnerabilites, Threats, Risks
- Security Policies and Models: Access Control, Information Flow, Non-Interference
- Practical Security Engineering: Model Engineering, Model, Specification, Model Implementation
- Security Mechanisms: FYI Authorization, Authentication, Cryptography
- Security Architectures: TCBs and Reference Monitors, Nizza,SELinux, Kerberos